Make sure that your internal network, application, or IoT object is protected against cyberattacks








We aim to help our clients in their security projects with flexibility and professionalism.
But since proof is more convincing than promises, here is what our clients say about us!
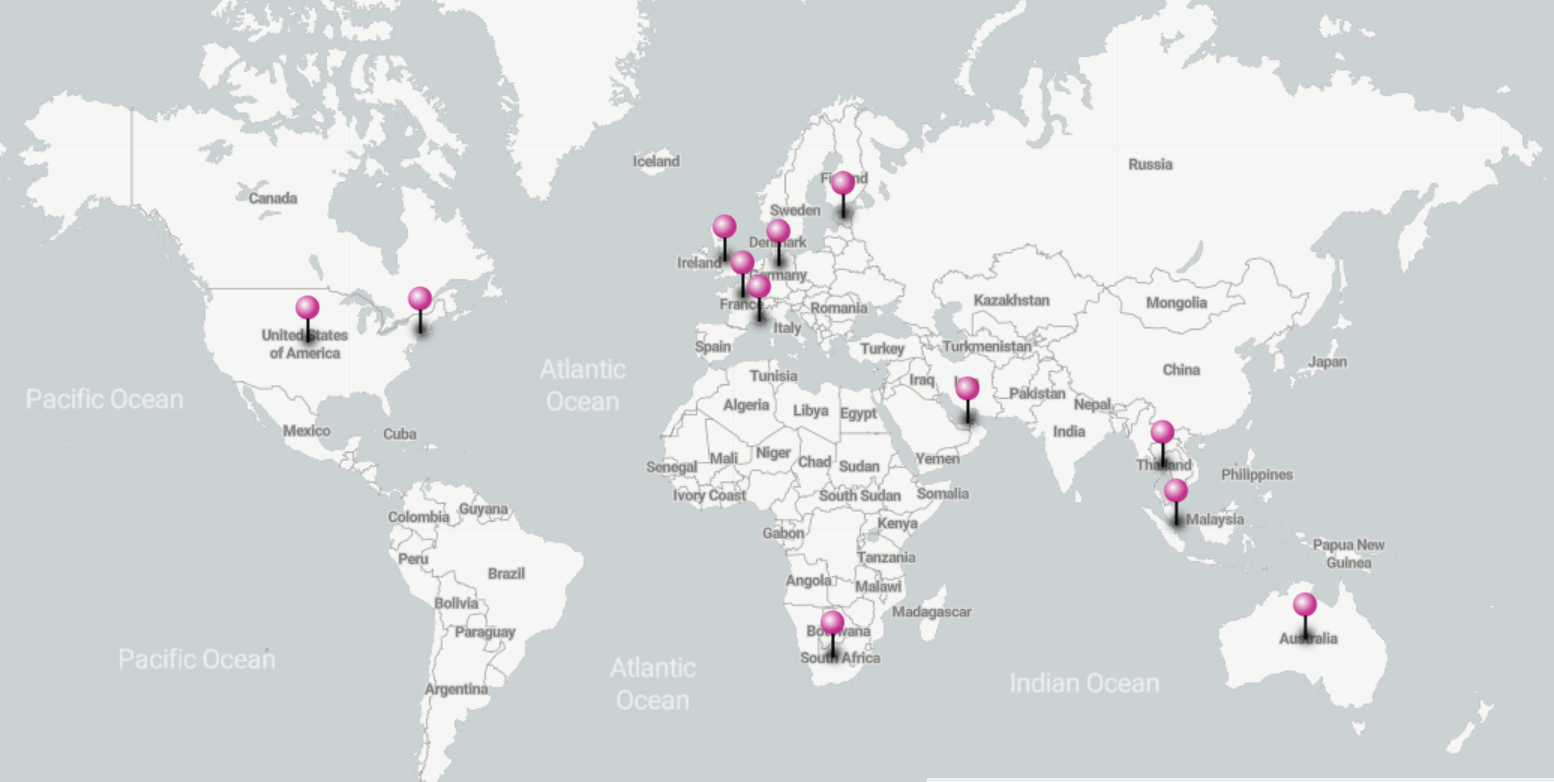
Location of our clients:
“We asked Unicorn Security to audit our server as well as our various frontends. The report was delivered very quickly with appropriate recommendations, it also showed a very good understanding of our business. I highly recommend and would happily work with them again.”
“We called upon the services of Antoine and Nathalie to carry out a Red Team audit. They were able to demonstrate the quality of their work by meeting all our requirements. They highlighted the areas of improvement, the defenses already in place and their impact on slowing down and blocking attackers.”
“Unicorn Security helped us assess the security of a unique application we are developing. We found them to be very collaborative, helpful and knowledgeable regarding the subject matter. I would definitely work with them again.”
“The Unicorn Security team is both professional and friendly. We benefited from an effective technical audit with adequate recommendations to strengthen the security of our information system. I highly recommend this very available and human-sized team.”
“We have performed a security review with Unicorn Security, involving social engineering attacks and an internal audit. We found their phishing emails to be extremely convincing, and it was a very good opportunity to test our reaction time, and our general security hygiene. The internal audit helped us consolidate defence-in-depth security measures, and was performed without any noticeable impact on the company's network. The report was delivered quickly after the end of the last phase, it was clear and precise.”
“I highly recommend Unicorn Security. They quickly understood our context and their audit enabled us to identify several points for improvement. We particularly appreciated their autonomy and their structured working method. It's a pleasure to work with people like that!”
“Unicorn Security helped the YOOS team assess the security hygiene of its complex ecosystem, consisting of hardware, OS, APIs and software configurations. More than the audit itself, tailored recommendations and a long lasting partnership resulted from it. This allows the YOOS team to strengthen its customers' trust and to have the confidence to build a safer future.”
“We requested Unicorn Security to help us with an Infrastructure Audit, as we control the full stack of our product. They have highlighted very critical points regarding system level configuration, network issues as well as several aspects of the application's flow. They were always available when we had questions regarding mitigations or further developments, and helped us put in place security measures. We care about our customer's data and there is no doubt it is now safer.”
“In order to raise the awareness of BTS SIO students of the F Le Dantec high school in Lannion, and to illustrate the skills of the cybersecurity block of this program, we have called upon Unicorn Security. We organized a videoconference with the co-founders of the company and the students. This time of presentation and exchange was very much appreciated by the students. We would like to thank them for their reactivity, professionalism and adaptability.”
Let's discuss the security of your internal system, application, website or IoT object!
Send us an email!
contact (at) unicornsecurity.io
Book a call with us
Select your preferred date and time and book your call
Join the discussion on Discord
Come and chat with us and the community on Discord